In the ever-evolving cybersecurity landscape, where threats are becoming increasingly sophisticated and adversaries are leveraging advanced technologies like AI, the role of cybersecurity professionals has never been more crucial. Check Point is at the forefront of this battle, shedding light on the pressing cyber threats and deploying innovative, proactive, and AI-powered strategies to combat them.
As cybercriminals refine their AI-based attack techniques, Check Point emphasizes the importance of continuous innovation and collaboration. "It's a cat-and-mouse game," acknowledged Moti Sagey, VP at Check Point. "The adversaries and defenders are always trying to stay one step ahead."
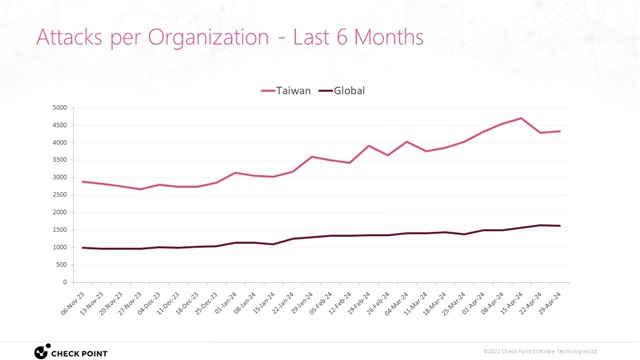
The Asia-Pacific region, particularly Taiwan, has become a hotbed for cyber attacks. This vulnerability is compounded by a sharp increase in ransomware attacks. According to Check Point's latest report, there has been a 90% increase in ransomware incidents compared to previous years, with over 68 attack groups involved. Sagey points out that the devastating impact of such attacks, ranging from reputational damage to operational paralysis, incur substantial financial losses.
AI and Machine Learning: A Double-Edged Sword
Another significant threat is state-affiliated hacktivism. Sagey highlights how cyber attacks are now an extension of geopolitical conflicts, citing examples like the Russia-Ukraine conflict and tensions in the Middle East. These attacks often aim to disrupt or manipulate public opinion, further complicating the global cyber threat landscape.
AI has become a double-edged sword in cybersecurity. While it offers powerful tools for defense, it also empowers attackers. "It becomes increasingly easy for attackers to attack," Sagey warns. Malicious actors can leverage AI to craft sophisticated phishing emails or even develop malware. Despite the safeguards in place, creative circumvention methods make these tools potent weapons in the hands of cybercriminals.
Integrating AI and machine learning technologies presents both opportunities and challenges in cybersecurity. On the one hand, Check Point leverages AI to enhance threat detection, prevention, and response capabilities. Sagey highlighted the company's use of 50 different AI engines to detect sophisticated malware. One notable application is 'Zero Phishing' system that analyzes emails in real-time, comparing visual similarities and domain histories to detect phishing attempts before users fall prey. Moreover, Check Point's Co-Pilot tool streamlines security administration by using AI to troubleshoot and resolve issues quickly.
However, the use of AI by cybercriminals to develop more advanced attack techniques is a growing concern. Sagey warned about the exponential use of deepfakes for social engineering and misinformation campaigns, citing incidents where deepfakes influenced election outcomes.
To address these risks, Check Point recommends a multi-layered approach. "You need to adopt innovation with safety in mind," Sagey advised. "We offer strategy consulting on the safe use of AI, secure development life cycles, and other measures to ensure the security of AI systems used by organizations."
A Unified Approach to Cybersecurity
Sagey emphasizes the importance of a consolidated cybersecurity platform. Check Point's Infinity Portal is a cloud-based platform that integrates various security solutions, providing a unified interface to manage network, cloud environments, mobile devices, endpoint, and email security. This strategy ensures that when one part of the network is compromised, the entire system can respond cohesively to contain and mitigate the threat.
Danny Yang, cyber security evangelist at Check Point, elaborates on the platform's capabilities, highlighting its AI-powered features that offer comprehensive protection across different attack vectors. This approach improves detection and response times and mitigates the issue of alert fatigue, where administrators are overwhelmed by numerous security alerts. He stated, "We want to consolidate all things together and use one pane for all consumption, making it easy for employees or IT admins to speak the same language about security operations."
Staying ahead of cyber threats requires a proactive and adaptive approach. Check Point focuses on preventing attacks rather than solely detecting and responding to them by integrating threat intelligence and leveraging AI-powered threat detection and prevention mechanisms. "We emphasize prevention because it's like the vaccination process in a pandemic," Sagey explained. This proactive stance offers significant benefits, including reduced risk exposure, faster incident response times, and lower overall costs associated with cyber incidents.
Securing Cloud and IoT Environments
As the Internet of Things (IoT) continues to proliferate, securing these devices has become increasingly important. Check Point's platform includes tools for discovering and fingerprinting IoT devices, allowing for precise and automated access control. This 'Zero Trust' approach ensures that each device is only permitted to communicate with its designated endpoints, significantly reducing the attack surface.
Check Point offers embedded "Nano Agent" technology that integrates security at the device firmware level during manufacturing. This "security by design" approach aims to mitigate supply chain attacks and harden IoT devices against vulnerabilities. "We emphasize security by design and go back to the origin to talk to supply chain vendors," Sagey said.
The cloud environment poses similar challenges. Yang notes that many organizations struggle with managing security across dispersed applications and data. Check Point provides visibility and control across multi-cloud deployments, enabling organizations to manage and secure their cloud assets from a single pane of glass. "We help our clients discover which Gen-AI tools their company uses and what the associated risks are," he explained. "We also have an AI Protect solution to provide threat prevention for our clients' AI computing or in-house Gen-AI services."
While AI offers powerful defensive tools for threat detection, prevention, and response, criminals can leverage it to develop sophisticated attack vectors like deepfakes and AI-generated malware. The cybersecurity battle demands continuous adaptation, with a multi-layered defense and industry collaboration proving vital to mitigating the evolving cyber threat landscape effectively.




